Securing Kerio Operator
Key measures
You can take the following measures to secure Kerio Operator:
- Restrict communication on firewall to necessary IP addresses and ports, especially if the PBX runs in the Internet.
- Restrict communication on the integrated firewall in Kerio Operator.
- Create strong SIP passwords.
- Restrict the number of attempts to enter SIP passwords.
- Using special rules, forbid international outgoing calls to countries you do not communicate with
- Restrict international outgoing calls to countries where you rarely call
- Encrypt your calls
- Encrypt data
The following sections describe these settings in detail.
Configuring firewall in local network
Kerio Operator is usually protected by firewall (in your local network or in the Internet). Certain ports need to be opened (or mapped) on firewall.
| Service (default port) | Outbound connection | Inbound connection |
|---|---|---|
| SIPSession Initiation Protocol - A communication protocol used for voice and video calls in Internet telephony or private IP telephone systems. (5060) | allow | allow for SIP servers of your provider |
| IMAP (143) | allow if integration with Kerio Connect is enabled and there is a firewall between Kerio Connect and Kerio Operator. | deny |
| LDAPLightweight Directory Access Protocol enables users to access centrally managed contacts. (389) | allow | deny |
| LDAPS (636) | allow | allow if you use mapping from Active Directory or Open Directory and there is a firewall between the directory service and Kerio Operator. |
| HTTP (80) | allow | deny |
| HTTPS (443) | allow | allow if you wish users to be able to connect to Kerio Phone from the Internet. |
| HTTPS (4021) | allow | allow if you wish users to be able to connect to the administration interface from the Internet. |
| STUN/TURN (3478) | allow | allow |
| STUN/TURN (3479) | allow | allow |
Configuring firewall integrated in Kerio Operator
Prepare groups of IP addresses which you wish to allow for individual services (create them in Definitions > IP Address Groups).
You can configure the integrated firewall in section Network > Firewall.
| Service | Recommendation |
|---|---|
| Web server | If you want to restrict connections to Kerio Operator administration and softphone, check this option and select an IP group with addresses from which access will be allowed. Bear in mind that all the PBXPrivate Branch Exchange - System that connects telephone extensions and switches calls. users should be allowed to connect to Kerio Phone at least from their own workstation. |
| SIP | We recommend to restrict the SIP protocol solely to your internal network and external IP addresses of your SIP provider. |
| Phone provisioning | For security reasons, we recommend to restrict automatic phone provisioning solely to your internal network because TFTPTrivial File Transfer Protocol - A simple protocol for transferring files. sends configuration data as plain text. |
| CRMCustomer Relationship Management - Strategies and technologies for managing and analyzing customer relationships. integration | For security reasons, we recommend to restrict communication solely to your internal network. |
| SNMPSimple Network Management Protocol - A protocol for gathering and organizing information about devices in IP networks, and changing devices behavior. monitoring | For security reasons, we recommend to restrict communication solely to your internal network and IP adressess where monitoring servers are running. |
NOTE
If the options are unchecked, no restrictions are set.
Data Encryption
You can enable encryption to ensure that Kerio Operator encrypts recorded calls, voicemail messages, logs, and configuration before writing it to the disk.
IMPORTANT
Encryption is bound to a specific storage device, so if you plan to change the hardware you must first disable encryption. Also, encryption results in more resources being utilized so performance maybe impacted.
Enabling Encryption
- In the Kerio Operator administration interface, go to Configuration > Advanced Options.
- Go to the Data Encryption tab.
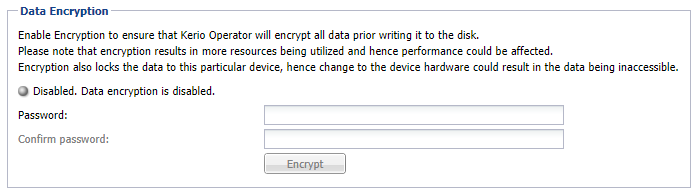
The data encryption tab
- Key-in the Password and re-enter to confirm the same.
IMPORTANT
Once encryption is enabled, the password cannot be changed. Remember this password, as you would require it to decrypt data.
- Click Encrypt and confirm the action.
Disabling Encryption
To decrypt: data and disable encryption:
- In the Kerio Operator administration interface, go to Configuration > Advanced Options.
- Go to the Data Encryption tab.
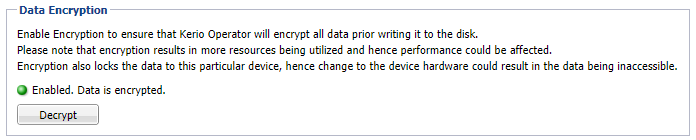
The data encryption tab
- Click Decrypt.
- Key-in the Password set while encrypting and confirm the action.
Configuring protection against password guesses
Login data guess is one of the most common attacks on a PBX. In Kerio Operator, attackers try to guess extension numbers and SIP passwords. This type of attack is defined by many unsuccessful attempts to enter extension number and SIP passwordA password for authenticating provided by a SIP provider. during a login. Kerio Operator security settings enable you to limit the number of attempts of a phone (both software and hardware) to connect to the PBX. Apply settings as described below:
- In the administration interface, go to Security.
- Set the limit of unsuccessful attempts (usually 3 to 10 attempts) and set the time period during which attempts will be counted. Setting the time period protects real users who have forgotten their password or who have made mistakes during several logins. When the time limit expires, they can try to login to the PBX again.
- Set the time during which Kerio Operator will block the source IP address.
- You can also enter an email address that will be used for sending warnings about blocked IP addresses.
How to recognize there has been an attack attempt
In log Security look for the
Authentication failed string. If there are many messages of
this kind, somebody is trying to use a dictionary attack.
What to do in case of an attack
In case of an attack, apply the following instructions as soon as possible:
- In section Status > Calls and in logs, look for information on which account has been abused.
- Change the SIP password of this account.
- Instruct users about handling their login details and secure behavior on the Internet.
- The PBX is blocked, so it needs to be unlocked again.